
National Security
Helping to protect against security threats and develop tailored secure system solutions.
Authorities, municipalities and companies are exposed to security threats daily. Cyber-attacks or insider threats can cause damage to society and our national security. National Security are measures to protect the most protection-worthy activities against espionage, sabotage, and terrorist crimes. AFRY are experts in identifying and implementing measures for physical security, information security and IT security, as well as personnel security.
We have several years of experience in accreditation and system development of IT systems for classified information, implementation of information security management systems and advisory within protective security.
AFRY is also experienced with working with both defense and civil authorities and we also have deep knowledge in specific regulations and standards, e.g., KSF, ISD, FM BMTS, FM IT-process, SSA, SSB, NIS, ISO27000.
Protective Security for companies and authorities.
Protective security refers to protecting information and activities of importance to Sweden’s security against espionage, sabotage, terrorist offences and certain other threats. Protective Security measures are regulated by the Protective Security Act and the Protective Security Ordinance.
AFRY helps both companies and authorities that operates within sectors such as the total defence, energy and water supplies, telecommunications, and transport to produce a documented protective security analysis to investigate the need for protective security.
In the analysis, what is to be protected is identified through a business analysis. Protective Security values are identified and measured against what is to be protected through a threat analysis and how it is to be protected is examined through a vulnerability assessment. Proposals for measures are described together with a protective security plan.
System development of secure IT systems for classified information
AFRY helps security-sensitive businesses with project management and development of system architectures in the development and procurement of secure IT systems for classified information.
AFRY makes sure to identify the business's needs, requirements, and threats to develop an adapted system solution that is secure. We have several years of experience in successful accreditations of IT systems for classified information.
Network and information security for critical and important services
An increasingly digitised society is also more exposed to external threats. For several years, the NIS directive, better known as the NIS Act, has been law in Sweden. Its goal is to enhance cybersecurity across the EU. The NIS directive was adopted in 2016 and subsequently, EU member states started to adopt national legislation that focuses on network and information systems critical for service availability within the EU to protect the Union’s critical infrastructure and economies.
The law aims to raise the minimum level of information security among providers of critical and important services to meet today's threats from, for example, ransomware or DDoS attacks.
The NIS Act requires systematic and risk-based information security work through, among other things, incident reporting, security measures and preventive continuity work. AFRY has extensive experience in implementing information security management systems, in line with ISO 27001, which is a requirement under the NIS Act.
AFRY helps companies investigate which parts of the business are affected by the NIS Act, respectively the Protective Security Act, and supports the implementation of concrete measures - for example by building NIS-regulated IT systems.
We offer
- Security Analysis
- Helping businesses understand how and where to invest to mitigate risk
- Accreditation
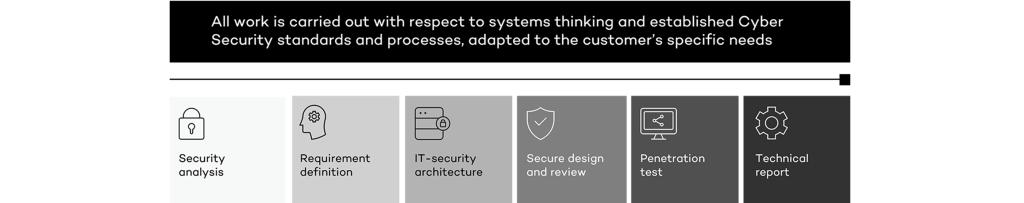
Security Analysis
-
Stakeholder analysis
-
Regulatory analysis
-
Security analysis
-
Business analysis
-
Risk & vulnerability analysis
-
-
Information security
-
Classification
-
Policies
-
Plans
-
-
Physical security
An understanding of how and where to invest to mitigate risk
-
Implement protective security measures and cyber security programs enabling structured decision-making.
-
Build a culture of risk awareness through education
-
Provide compliance with laws and regulations
Accreditation
-
Requirement identification and management
-
Requirements are identified through a security analysis
-
-
Requirements are identified through a security analysis
-
Architecture definition
-
Define a security architecture that fulfills the identified requirements and at the same time fulfills your business needs regarding functionality and availability
-
-
Define a security architecture that fulfills the identified requirements and at the same time fulfills your business needs regarding functionality and availability
-
Design & review
-
Detailed design and review of IT-systems
-
-
Detailed design and review of IT-systems
-
Testing
-
Provide security testing that assures that the security measures and design meet the requirements
-
-
Provide security testing that assures that the security measures and design meet the requirements
-
Technical report
-
Through the documentation, traceability is created from your business needs and requirements to the implemented and tested solution
-
-
Through the documentation, traceability is created from your business needs and requirements to the implemented and tested solution









