
Penetration Testing
Penetration Testing helps organisations identify and prioritise vulnerabilities in their systems and assess their impact.
There will always be vulnerabilities in your IT and OT-environments, and, therefore, there will always be threat actors seeking to exploit your vulnerabilities. With regular Penetration Testing we will enable your organisation to assess which vulnerabilities can be exploited in your organisation’s attack surface, and, further, to prioritise which vulnerabilities need quick mitigation. Additionally, when a new serious vulnerability is published, regular Penetration Testing will help you to rapidly assess whether your organisation is impacted, and to what extent.
A Penetration Test is normally executed according to a method that mimics the actions of a real attacker, consisting of a number of steps which are summarised below:
-
Reconnaissance – Specify scope and collecting information about test scope from public sources
-
Scanning & Enumeration - Scanning for open services on servers and applications, and enumerate user accounts, password hashes, hidden directories, etc.
-
Exploitation – Based on previous findings, identity and exploit vulnerabilities on hosts
-
Escalation – Further escalate privileges to gain additional access
-
Get interactive – set up a shell on attacked host and perform actions such as installing a backdoor to re-enter the exploited host at a later stage
-
Document & Demonstrate Access – write a comprehensive report and demonstrate results to customer
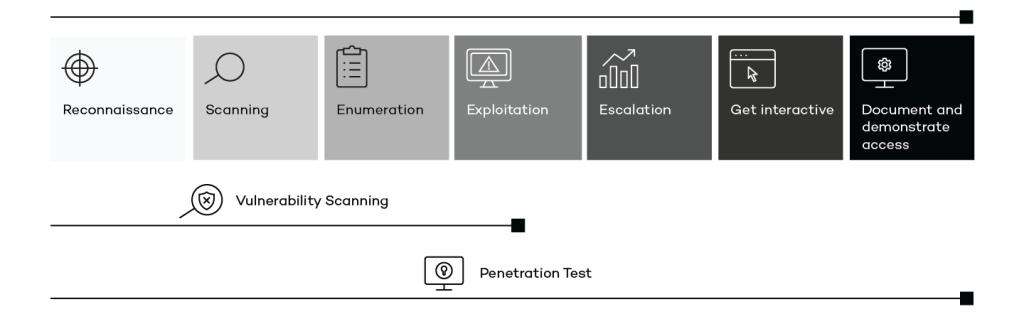

All these steps are not always executed. In a Vulnerability Scanning, vulnerabilities are identified and prioritized according to severity, but no exploitation and escalation is performed. In a Penetration Test, on the other hand, a number of vulnerabilities are often selected for exploitation and demonstration.
When setting up the scope for a Penetration Test, a number of aspects have to be decided:
-
Will the test be performed from an external or internal network, or a combination of both?
-
Should it be a black box test, where the attacker has no prior knowledge about the tested scope, or a white box test, where the tested has prior knowledge about e.g., the network infrastructure?
-
Will the test be performed on a traditional IT-environment containing sensitive information or an OT-environment with e.g., industrial control systems controlling critical infrastructure?
A Security Analysis complements the Penetration Test by testing various security mechanisms to assess the security of a system or an IT-environment, such as
-
The existence of security processes such as routines for patching or handling security incidents
-
If centralised logging is implemented
-
If these is a SIEM in place for detecting intrusions
-
How authentication and authorisation is implemented
-
If operating systems are hardened against security benchmarks
-
Configuration of network devices such as firewalls, switches and routers
A comprehensive report is always created after the Penetration Test, containing among others the following:
-
An executive summary of the performed Penetration Test
-
A list of identified vulnerabilities attributed with a severity level
-
Recommendations regarding which vulnerabilities to mitigate first

Interested in our offering? Contact us!
